Het arrangement Privacy in Research Light is gemaakt met Wikiwijs van Kennisnet. Wikiwijs is hét onderwijsplatform waar je leermiddelen zoekt, maakt en deelt.
- Auteur
- Laatst gewijzigd
- 04-02-2019 13:06:58
- Licentie
-
Dit lesmateriaal is gepubliceerd onder de Creative Commons Naamsvermelding 4.0 Internationale licentie. Dit houdt in dat je onder de voorwaarde van naamsvermelding vrij bent om:
- het werk te delen - te kopiëren, te verspreiden en door te geven via elk medium of bestandsformaat
- het werk te bewerken - te remixen, te veranderen en afgeleide werken te maken
- voor alle doeleinden, inclusief commerciële doeleinden.
Meer informatie over de CC Naamsvermelding 4.0 Internationale licentie.
Aanvullende informatie over dit lesmateriaal
Van dit lesmateriaal is de volgende aanvullende informatie beschikbaar:
- Eindgebruiker
- leerling/student
- Moeilijkheidsgraad
- gemiddeld
Gebruikte Wikiwijs Arrangementen
SURF Privacy Awareness. (z.d.).
Privacy in Onderzoek Light
 From 25 May 2018, the General Data Protection Regulation (GDPR) applies. This means that from this date the same privacy legislation applies in the entire European Union. The Dutch Data Protection Act (Wbp) will no longer apply from this date.
From 25 May 2018, the General Data Protection Regulation (GDPR) applies. This means that from this date the same privacy legislation applies in the entire European Union. The Dutch Data Protection Act (Wbp) will no longer apply from this date.



 The GDPR applies to personal data. Therefore, the first question to ask is always: do you process personal data in the study? If this is not the case, then the GDPR does not apply. If you do process personal data, however, there are five points you need to remember to ensure maximum protection of such data in your study.
The GDPR applies to personal data. Therefore, the first question to ask is always: do you process personal data in the study? If this is not the case, then the GDPR does not apply. If you do process personal data, however, there are five points you need to remember to ensure maximum protection of such data in your study.





 Privacy filter: a special type of foil that can be used on any laptop or desktop screen. It reduces the viewing angle, safeguarding data from prying eyes, which is useful, especially if you travel extensively for work. Search for ‘privacy filter laptop’ to find a suitable type.
Privacy filter: a special type of foil that can be used on any laptop or desktop screen. It reduces the viewing angle, safeguarding data from prying eyes, which is useful, especially if you travel extensively for work. Search for ‘privacy filter laptop’ to find a suitable type. Webcam cover: prevents unauthorised viewing from your webcam. A webcam cover is a 'small lock’ that is easy to install and can cover the webcam completely, if desired, making unauthorised viewing a thing of the past. Search for ‘webcam cover’ to find a suitable type.
Webcam cover: prevents unauthorised viewing from your webcam. A webcam cover is a 'small lock’ that is easy to install and can cover the webcam completely, if desired, making unauthorised viewing a thing of the past. Search for ‘webcam cover’ to find a suitable type. Encryption of the hard drive: encryption protects the data on the drive from unauthorised access, as the drive can be easily removed from your laptop and be effortlessly read by a PC. BitLocker Drive Encryption is a good option for Windows, and FileVault will get the job done on Macs.
Encryption of the hard drive: encryption protects the data on the drive from unauthorised access, as the drive can be easily removed from your laptop and be effortlessly read by a PC. BitLocker Drive Encryption is a good option for Windows, and FileVault will get the job done on Macs. Terms of service (ToS) reader: many online services have included provisions in their ToS as to what they can do with your data. There are add-ons available for your browser to facilitate assessment of these often lengthy ToS documents. These add-ons provide additional information about the risks you may encounter when using the service.
Terms of service (ToS) reader: many online services have included provisions in their ToS as to what they can do with your data. There are add-ons available for your browser to facilitate assessment of these often lengthy ToS documents. These add-ons provide additional information about the risks you may encounter when using the service. Anti virus software: good anti-virus software and regular system updates are essential to prevent malicious attacks and unauthorised access to your computer or laptop. This software keeps your computer clean and secure.
Anti virus software: good anti-virus software and regular system updates are essential to prevent malicious attacks and unauthorised access to your computer or laptop. This software keeps your computer clean and secure.
 Privacy by Design: one of the key starting points for the proper handling of personal data. It means that not only do you clearly describe in your research plan how you will safeguard privacy, but also that you will take the appropriate technical and organisational measures for each step in the research process. Watch the video below before trying to complete the exercise:
Privacy by Design: one of the key starting points for the proper handling of personal data. It means that not only do you clearly describe in your research plan how you will safeguard privacy, but also that you will take the appropriate technical and organisational measures for each step in the research process. Watch the video below before trying to complete the exercise:
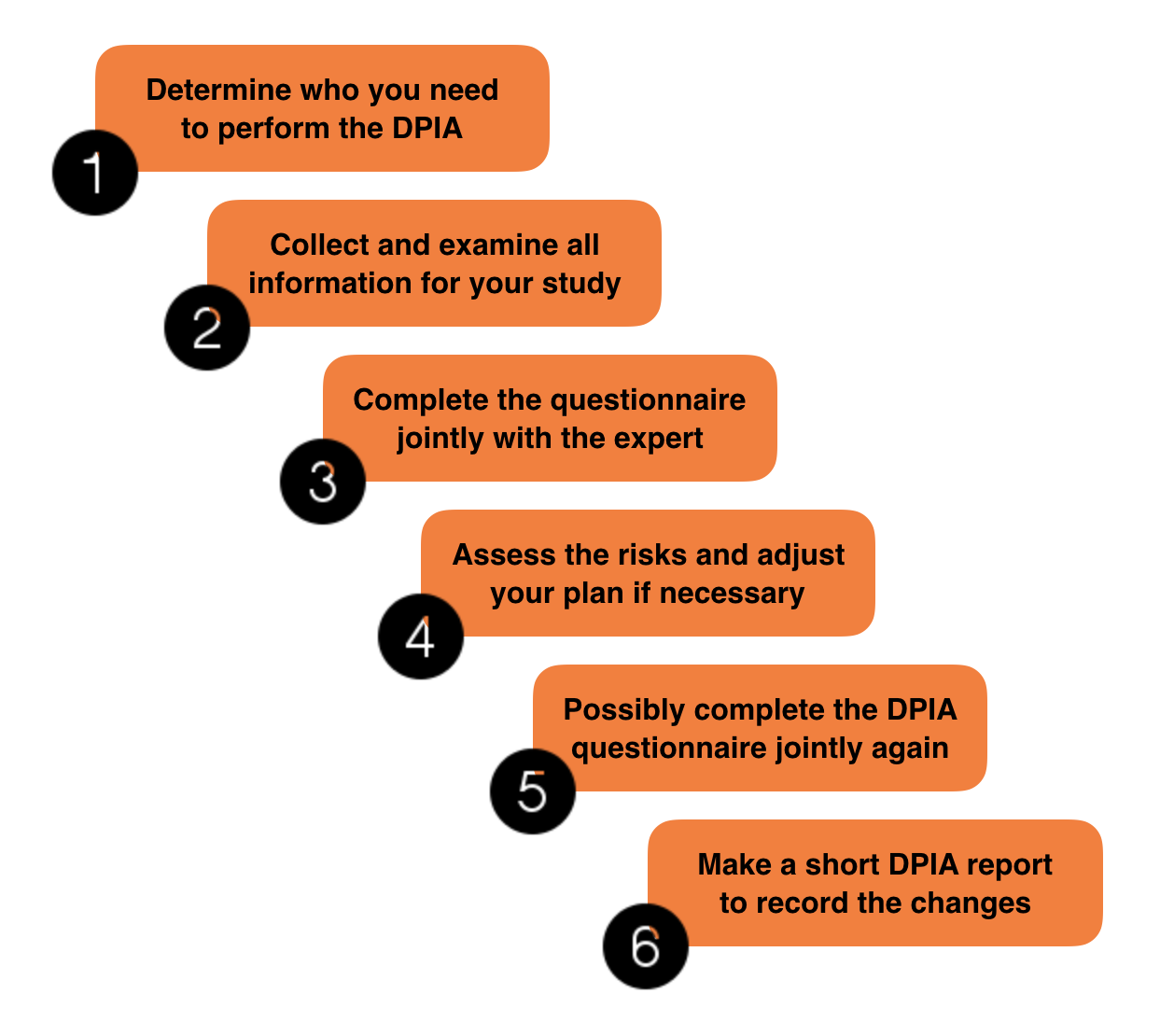
 How do you, as a researcher, know whether you have taken all possible measures to protect the personal data in your study? By using a Data Protection Impact Assessment (DPIA). The Dutch name of the DPIA is 'gegevensbeschermings-effectbeoordeling'.
How do you, as a researcher, know whether you have taken all possible measures to protect the personal data in your study? By using a Data Protection Impact Assessment (DPIA). The Dutch name of the DPIA is 'gegevensbeschermings-effectbeoordeling'.