Het arrangement Privacy in Research is gemaakt met Wikiwijs van Kennisnet. Wikiwijs is hét onderwijsplatform waar je leermiddelen zoekt, maakt en deelt.
- Auteur
- Laatst gewijzigd
- 04-02-2019 13:06:46
- Licentie
-
Dit lesmateriaal is gepubliceerd onder de Creative Commons Naamsvermelding 4.0 Internationale licentie. Dit houdt in dat je onder de voorwaarde van naamsvermelding vrij bent om:
- het werk te delen - te kopiëren, te verspreiden en door te geven via elk medium of bestandsformaat
- het werk te bewerken - te remixen, te veranderen en afgeleide werken te maken
- voor alle doeleinden, inclusief commerciële doeleinden.
Meer informatie over de CC Naamsvermelding 4.0 Internationale licentie.
This online training is produced by:
Marlon Domingus (DPO, Erasmus University Rotterdam)
Sander van Acht (Flooow, educational concept)
Maarten van der Schaal (Nieuwbericht, slidedesign)
Photo-credits:
Aanvullende informatie over dit lesmateriaal
Van dit lesmateriaal is de volgende aanvullende informatie beschikbaar:
- Eindgebruiker
- leerling/student
- Moeilijkheidsgraad
- gemiddeld
Gebruikte Wikiwijs Arrangementen
SURF Privacy Awareness. (2018).
Privacy in Onderzoek

 From 25 May 2018, the General Data Protection Regulation (GDPR) applies. This means that from this date the same privacy legislation applies in the entire European Union. The Dutch Data Protection Act (Wbp) will no longer apply from this date.
From 25 May 2018, the General Data Protection Regulation (GDPR) applies. This means that from this date the same privacy legislation applies in the entire European Union. The Dutch Data Protection Act (Wbp) will no longer apply from this date.
 You learn what the GDPR entails;
You learn what the GDPR entails;


 What is your current knowledge of the GDPR? How effective can you choose adequate technical and organisational measures to be taken in the context of a certain research project? In order to test yourself, we offer you three introductory cases. Please read each case carefully before trying to answer the questions.
What is your current knowledge of the GDPR? How effective can you choose adequate technical and organisational measures to be taken in the context of a certain research project? In order to test yourself, we offer you three introductory cases. Please read each case carefully before trying to answer the questions. :
:  :
:  :
: 









 You see from the three cases that specific measures are required for each study to ensure correct handling of personal data. However, there are also general ‘quick wins’ for researchers: simple adjustments in your working method that ensure considerable extra security. This page contains a brief overview.
You see from the three cases that specific measures are required for each study to ensure correct handling of personal data. However, there are also general ‘quick wins’ for researchers: simple adjustments in your working method that ensure considerable extra security. This page contains a brief overview.
 Privacy filter: A special type of foil that can be applied to every laptop or desktop screen. It ensures that the viewing angle is significantly reduced to make it more difficult for other people to view your screen. Useful when you are working a lot on the go. Search for ‘privacy filter laptop’ to find a suitable type.
Privacy filter: A special type of foil that can be applied to every laptop or desktop screen. It ensures that the viewing angle is significantly reduced to make it more difficult for other people to view your screen. Useful when you are working a lot on the go. Search for ‘privacy filter laptop’ to find a suitable type.
 Webcam cover: Without you noticing it, malicious people can view through your webcam. A webcam cover is a ‘small lock’ that is simple to apply and can fully cover the webcam when required. This makes viewing by others a thing of the past. Search for ‘webcam cover’ to find a suitable type.
Webcam cover: Without you noticing it, malicious people can view through your webcam. A webcam cover is a ‘small lock’ that is simple to apply and can fully cover the webcam when required. This makes viewing by others a thing of the past. Search for ‘webcam cover’ to find a suitable type.
 Encryption of the hard drive: With encryption the data on the drive is secured against unauthorised access, as this drive can be easily removed from your laptop and be read effortlessly by a pc. For Windows computers, BitLocker Drive Encryption is a good option, for Macs this is FileVault.
Encryption of the hard drive: With encryption the data on the drive is secured against unauthorised access, as this drive can be easily removed from your laptop and be read effortlessly by a pc. For Windows computers, BitLocker Drive Encryption is a good option, for Macs this is FileVault. Terms of service reader: Many online services have included provisions in their ‘terms of service’ on what they can do with your data. There are add-ons available for your browser to make it easier to asses these often lengthy ‘terms of service’ documents. These add-ons give a quick insight into the risks you run by using the service.
Terms of service reader: Many online services have included provisions in their ‘terms of service’ on what they can do with your data. There are add-ons available for your browser to make it easier to asses these often lengthy ‘terms of service’ documents. These add-ons give a quick insight into the risks you run by using the service. Anti virus software: To prevent malicious people from getting access to your computer or laptop, quality anti-virus software and regular installing of updates are important. This software keeps your computer clean and safe.
Anti virus software: To prevent malicious people from getting access to your computer or laptop, quality anti-virus software and regular installing of updates are important. This software keeps your computer clean and safe.
 Personal data. Why would you handle it with care? It only takes extra time and trouble to properly arrange it all. No... It can even offer you a lot of benefits. Really. Here are four reasons why careful handling of personal data may be important.
Personal data. Why would you handle it with care? It only takes extra time and trouble to properly arrange it all. No... It can even offer you a lot of benefits. Really. Here are four reasons why careful handling of personal data may be important.



 The new privacy law which takes effect on 25 May 2018, is called the General Data Protection Regulation or GDPR. This regulation applies to all persons in organisations that process personal data of European citizens, therefore including staff from the university or university of applied sciences. This page provides a brief introduction to the GDPR and sets out what is specifically relevant for researchers.
The new privacy law which takes effect on 25 May 2018, is called the General Data Protection Regulation or GDPR. This regulation applies to all persons in organisations that process personal data of European citizens, therefore including staff from the university or university of applied sciences. This page provides a brief introduction to the GDPR and sets out what is specifically relevant for researchers.
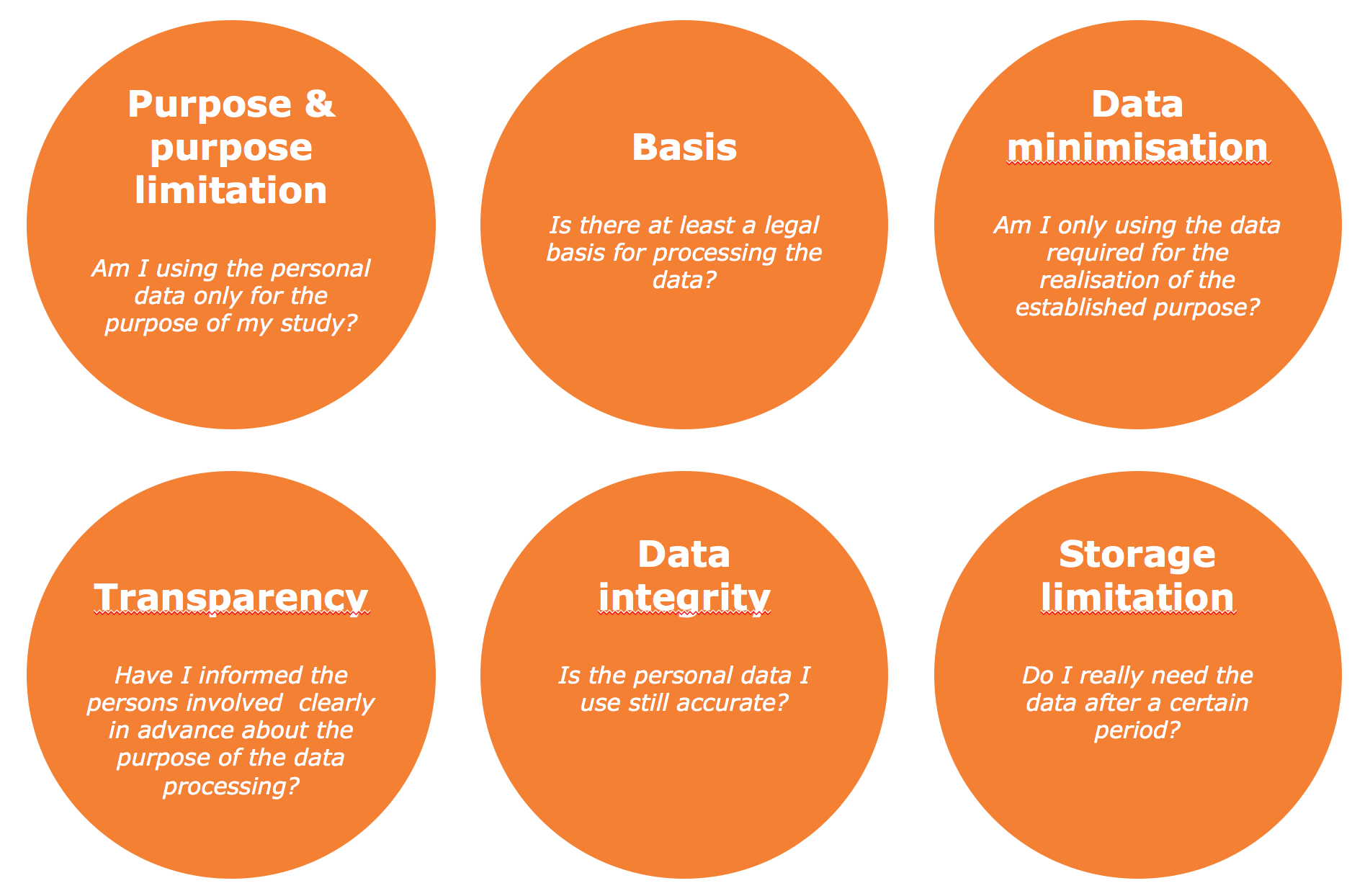
 Privacy by Design. One of the key starting points for proper handling of personal data. It means that you do not only describe clearly in your research plan how you will safeguard privacy, but also that you take the correct technical and organisational measures for every step in the research process. This exercise will show you which they are.
Privacy by Design. One of the key starting points for proper handling of personal data. It means that you do not only describe clearly in your research plan how you will safeguard privacy, but also that you take the correct technical and organisational measures for every step in the research process. This exercise will show you which they are. Does the study involve collaboration of public or private parties?
Does the study involve collaboration of public or private parties? Does the study assume existing data sets or does the study only create a new data set?
Does the study assume existing data sets or does the study only create a new data set? Do the researchers use new technologies or very extensive data sets in the study?
Do the researchers use new technologies or very extensive data sets in the study? How do you, as a researcher, know you have taken all possible measures to protect the personal data in your study? You use a Data Protection Impact Assessment (DPIA). In Dutch: a 'gegevensbeschermings-effectbeoordeling'.
How do you, as a researcher, know you have taken all possible measures to protect the personal data in your study? You use a Data Protection Impact Assessment (DPIA). In Dutch: a 'gegevensbeschermings-effectbeoordeling'.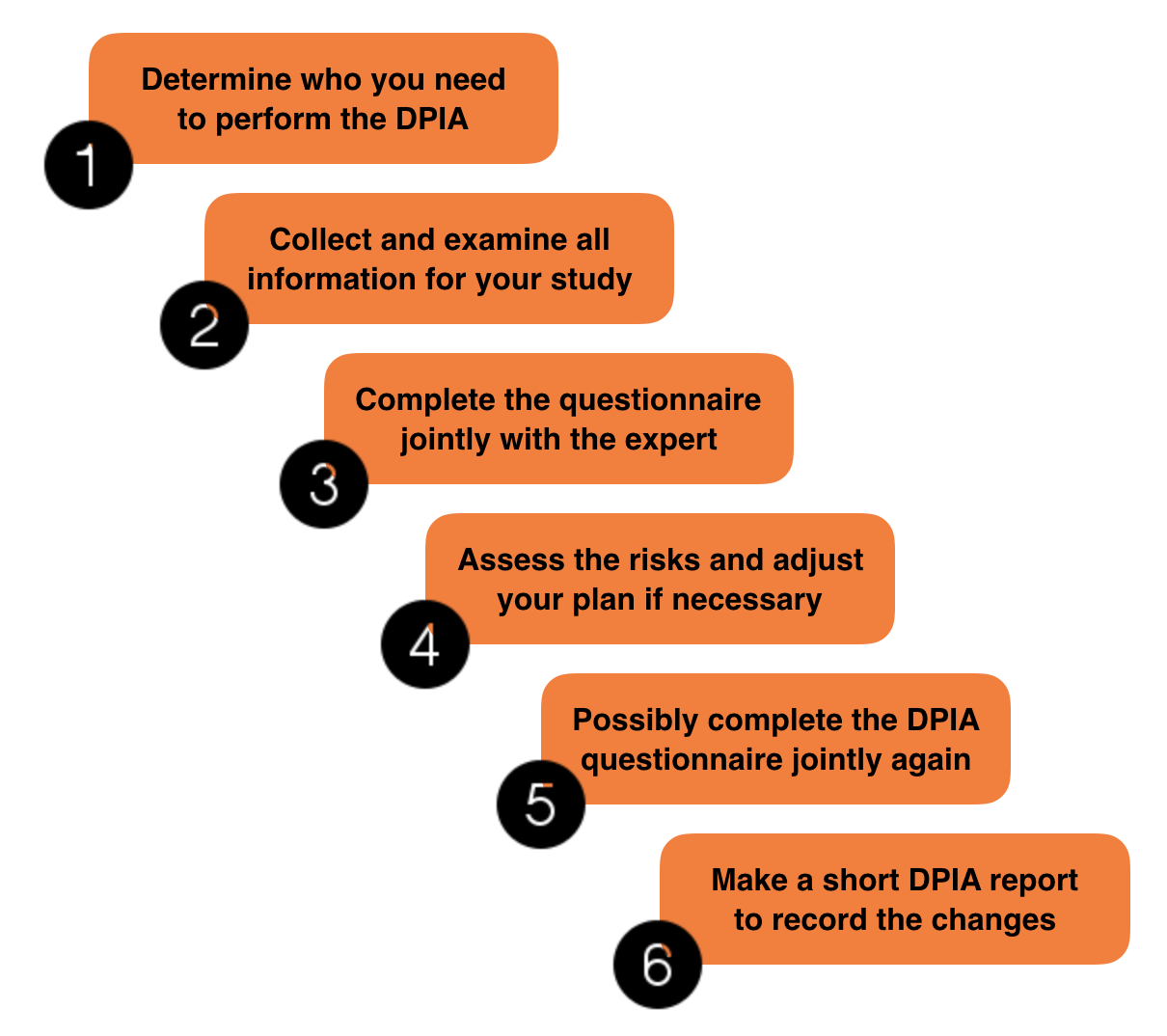


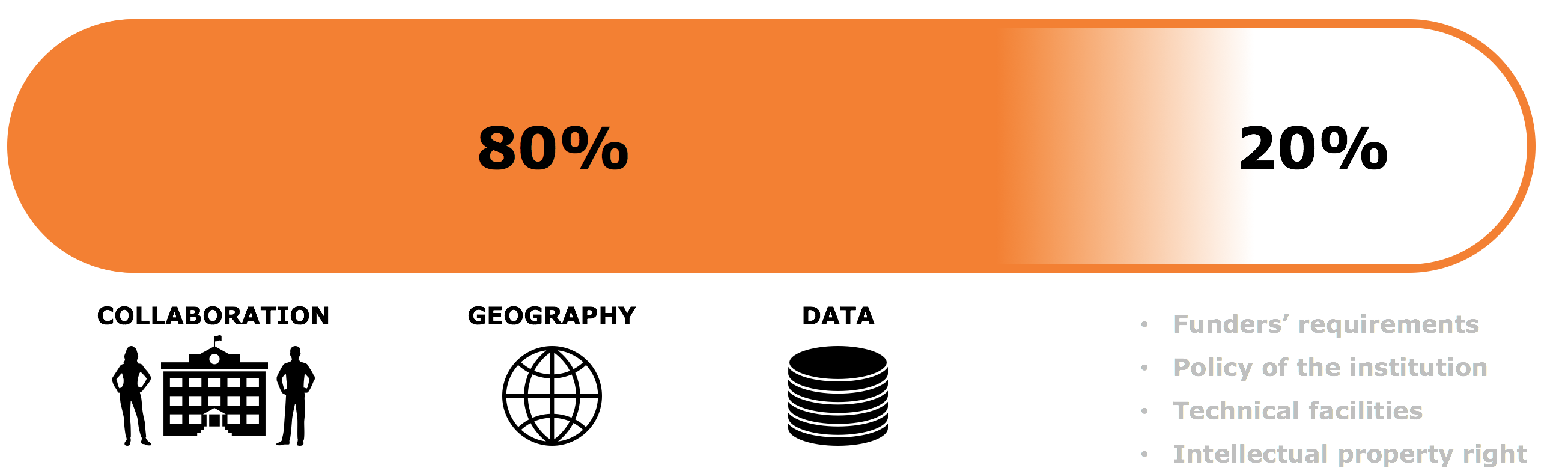
 The way in which you collaborate with other parties in your study may have consequences for the measures you have to take in the GDPR. For instance, entering into contracts governing access to certain data. The privacy expert in your organisation can tell you the exact measures based on your situation.
The way in which you collaborate with other parties in your study may have consequences for the measures you have to take in the GDPR. For instance, entering into contracts governing access to certain data. The privacy expert in your organisation can tell you the exact measures based on your situation.
 Also, the geographical delineation of your study has consequences for the measures you have to take. Not only the countries that are involved in the study, but for instance also the countries where servers are located storing the data of your study. The privacy expert in your organisation can tell you the exact measures based on your situation.
Also, the geographical delineation of your study has consequences for the measures you have to take. Not only the countries that are involved in the study, but for instance also the countries where servers are located storing the data of your study. The privacy expert in your organisation can tell you the exact measures based on your situation.
 If you do not use personal data in your study, the GDPR does not apply. If (part of) your data does consist of personal data, you have to take measures. The type of data you use shall determine the kind of measures. The privacy expert in your organisation can tell you the exact measures based on your situation.
If you do not use personal data in your study, the GDPR does not apply. If (part of) your data does consist of personal data, you have to take measures. The type of data you use shall determine the kind of measures. The privacy expert in your organisation can tell you the exact measures based on your situation.


