Het arrangement Digital license 'Employee' is gemaakt met Wikiwijs van Kennisnet. Wikiwijs is hét onderwijsplatform waar je leermiddelen zoekt, maakt en deelt.
- Auteur
- Laatst gewijzigd
- 04-12-2020 16:31:07
- Licentie
-
Dit lesmateriaal is gepubliceerd onder de Creative Commons Naamsvermelding 4.0 Internationale licentie. Dit houdt in dat je onder de voorwaarde van naamsvermelding vrij bent om:
- het werk te delen - te kopiëren, te verspreiden en door te geven via elk medium of bestandsformaat
- het werk te bewerken - te remixen, te veranderen en afgeleide werken te maken
- voor alle doeleinden, inclusief commerciële doeleinden.
Meer informatie over de CC Naamsvermelding 4.0 Internationale licentie.
This ‘Digital Certificate in Privacy & Security for Employees’ course was developed with the help of various people:
Commissioning party: Albert Hankel (SURF)
Production of e-learning module: Sander van Acht (Flooow)
Experts involved: Anita Polderdijk-Rijntjes (Security & Privacy Advisor and Data Protection Officer, Windesheim University of Applied Sciences)
Astrid Gravenbeek (Data Protection Officer, Leiden University)
Gerrit Vissinga (Information management advisor, Windesheim University of Applied Sciences)
Image credits:
Photo by Alexander Sinn on Unsplash
Photo by Ben Kolde on Unsplash
Photo by Markus Spiske on Unsplash
Photo by Eric Rothermel on Unsplash
Photo by Jilbert Ebrahimi on Unsplash
Photo by Markus Spiske on Unsplash
Photo by Kelly Sikkema on Unsplash
Aanvullende informatie over dit lesmateriaal
Van dit lesmateriaal is de volgende aanvullende informatie beschikbaar:
- Eindgebruiker
- leerling/student
- Moeilijkheidsgraad
- gemiddeld
- Studiebelasting
- 4 uur 0 minuten


 Do you remember the game ‘Who am I?’ on the right? In this game, you combine various kinds of personal data, so you can eventually guess the identity of the person concerned correctly. It works the same way with your own personal data. The mere fact that you have brown hair is not personal data, but it is considered personal data if you are the only person in your class with that colour hair. On its own, your first name is in many cases insufficient to be able to identify you, but it is enough if your last name and house number are also known.
Do you remember the game ‘Who am I?’ on the right? In this game, you combine various kinds of personal data, so you can eventually guess the identity of the person concerned correctly. It works the same way with your own personal data. The mere fact that you have brown hair is not personal data, but it is considered personal data if you are the only person in your class with that colour hair. On its own, your first name is in many cases insufficient to be able to identify you, but it is enough if your last name and house number are also known. Goal: based on the insights you have gained into the applications used in a team/department (which are not part of the standard range), determine in consultation which applications are desirable and/or strictly necessary.
Goal: based on the insights you have gained into the applications used in a team/department (which are not part of the standard range), determine in consultation which applications are desirable and/or strictly necessary.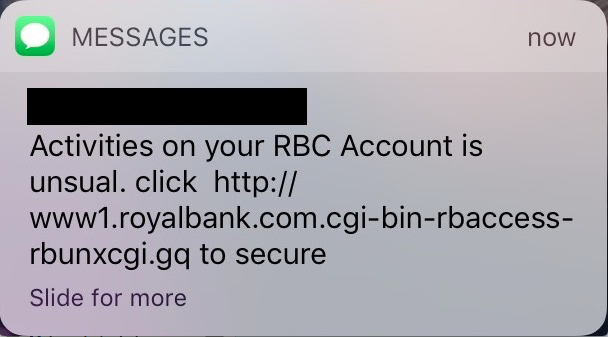 When we hear the word phishing, it often brings to mind the weird emails or text messages everyone receives once in a while – the kind that are not very well written and include a link referring to a strange URL and vague logos. Those are clearly not to be trusted. But these days many phishing messages are quite sophisticated and difficult to distinguish from the real thing. It requires that you, a human being, have a very critical mindset about all communication that comes your way.
When we hear the word phishing, it often brings to mind the weird emails or text messages everyone receives once in a while – the kind that are not very well written and include a link referring to a strange URL and vague logos. Those are clearly not to be trusted. But these days many phishing messages are quite sophisticated and difficult to distinguish from the real thing. It requires that you, a human being, have a very critical mindset about all communication that comes your way. Goal: to become aware of the degree to which others can easily find sensitive data such as personal data.
Goal: to become aware of the degree to which others can easily find sensitive data such as personal data.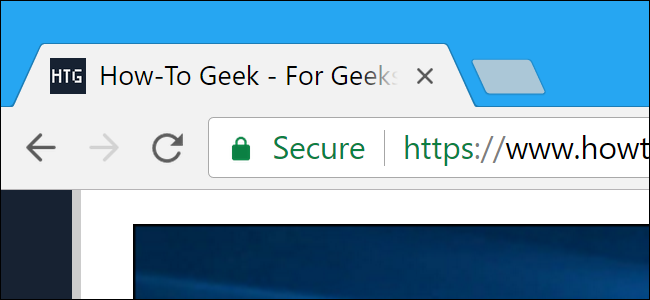 When a padlock icon appears next to the URL, that means that the website URL is preceded by ‘HTTPS://’. The ‘S’ in ‘HTTPS’ stands for 'secure’; this indicates that the website transmits all traffic in encrypted form. By clicking on the padlock icon, you can find further information about the website and check whether you are dealing with the right website.
When a padlock icon appears next to the URL, that means that the website URL is preceded by ‘HTTPS://’. The ‘S’ in ‘HTTPS’ stands for 'secure’; this indicates that the website transmits all traffic in encrypted form. By clicking on the padlock icon, you can find further information about the website and check whether you are dealing with the right website.
 Goal: to learn that you must always lock your computer screen if you will be away from your computer.
Goal: to learn that you must always lock your computer screen if you will be away from your computer. Goal: to become aware of how easily people may divulge privacy-sensitive data such as passwords both online and offline.
Goal: to become aware of how easily people may divulge privacy-sensitive data such as passwords both online and offline. Goal: to become aware of the degree to which you and your colleagues leak data within your team/department and come up with measures together to prevent this.
Goal: to become aware of the degree to which you and your colleagues leak data within your team/department and come up with measures together to prevent this. Goal: to achieve your team's objectives through collaboration and thus raise awareness with regard to privacy and security.
Goal: to achieve your team's objectives through collaboration and thus raise awareness with regard to privacy and security.